Greetings! I'm Aneesh Sreedharan, CEO of 2Hats Logic Solutions. At 2Hats Logic Solutions, we are dedicated to providing technical expertise and resolving your concerns in the world of technology. Our blog page serves as a resource where we share insights and experiences, offering valuable perspectives on your queries.

Quick Summary
ERP systems hold your most sensitive business data, making security and compliance critical for avoiding costly breaches and regulatory fines. US businesses must follow various laws like SOX, HIPAA, and state privacy regulations while implementing basic protections like strong passwords, data encryption, and careful vendor selection. Getting ERP security right protects your business from million-dollar breaches and keeps you compliant with regulations, while poor security can result in devastating fines, lawsuits, and lost customer trust.
Enterprise Resource Planning (ERP) systems have become the central nervous system of modern businesses. This system assists in integrating everything from financial management and human resources to supply chain operations and business intelligence.
With ERP systems housing vast amounts of sensitive business data. All the information, ranging from financial records and employee information to proprietary processes and strategic insights, the stakes for proper security and compliance management are exceptionally high. A single breach or compliance failure can result in millions in damages, regulatory penalties, and irreparable harm to business reputation. Learn how to secure data and understand compliance in your ERP systems.
Why ERP Security and Compliance Matter More Than Ever
ERP systems are particularly attractive targets for cybercriminals because they contain comprehensive business data in centralized locations. Unlike standalone applications, ERP platforms integrate multiple business functions. This means a single security breach can expose major data.
The regulatory landscape has also intensified significantly. US businesses now navigate complex requirements from federal agencies, state governments, and industry-specific bodies. This is done while managing the inherent risks of cloud-based ERP deployments, third-party integrations, and remote access requirements. This has become essential during the digital transformation accelerated by recent global events.
Critical US Compliance Frameworks for ERP Systems
There are certain frameworks set in the US for ERP systems. Take a look at some:
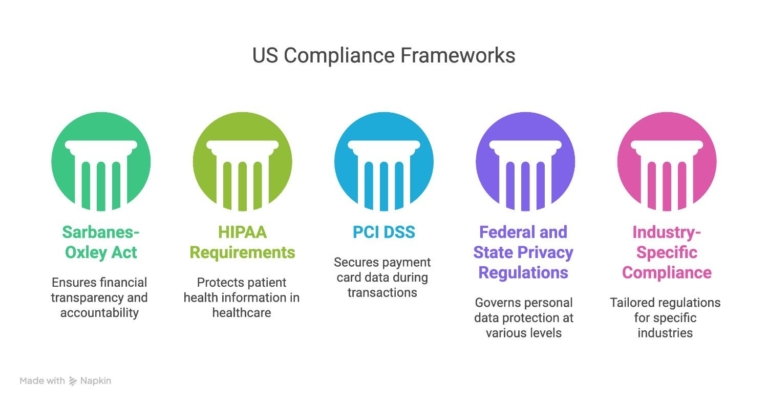
Sarbanes-Oxley Act (SOX) Compliance
For publicly traded companies, SOX compliance represents one of the most significant regulatory challenges in ERP management. Section 404 requires companies to establish and maintain adequate internal controls over financial reporting. This can directly impact how ERP systems handle financial data processing, approval workflows, and audit trails.
Key SOX requirements for ERP systems include implementing proper segregation of duties. This means tracking all financial transactions and maintaining accurate reports. Clear procedures are needed for any changes to financial controls.
HIPAA Requirements for Healthcare ERP
Healthcare organizations using ERP systems must ensure their platforms comply with HIPAA’s Privacy and Security Rules when processing Protected Health Information (PHI). This includes implementing administrative safeguards like workforce training and access management, physical safeguards for ERP infrastructure, and technical safeguards including encryption and access controls.
ERP systems in healthcare environments require specific attention to business associate agreements with vendors, risk assessments for PHI processing modules, and incident response procedures tailored to healthcare data breaches.
PCI DSS for Payment Processing
Organizations using ERP systems to process, store, or transmit credit card information must maintain PCI DSS compliance. This creates unique challenges because ERP systems often integrate payment processing with other business functions, requiring careful network segmentation and data flow analysis.
Critical PCI requirements include maintaining secure network architectures around ERP payment modules, implementing strong access control measures, regularly monitoring and testing ERP networks handling cardholder data, and maintaining comprehensive information security policies.
Federal and State Privacy Regulations
ERP systems often process personal information subject to various privacy laws. The California Consumer Privacy Act (CCPA) and other emerging state privacy laws create obligations for businesses using ERP systems to track, manage, and protect personal information throughout their operations.
For businesses with international operations, GDPR compliance requirements may also apply to ERP systems processing EU resident data, requiring careful attention to data processing agreements, cross-border data transfers, and individual privacy rights.
Industry-Specific ERP Compliance
Different industries face unique regulatory requirements that impact ERP system design and operation. Financial services firms must consider GLBA requirements and FFIEC guidance, while government contractors face DFARS cybersecurity requirements and NIST framework implementation mandates.
Manufacturing companies may need to address FDA regulations for quality management systems integration, while energy sector organizations must consider NERC CIP requirements for critical infrastructure protection.
Essential Security Controls for ERP Systems
Take a look at some of the security controls for ERP systems.
Identity and Access Management
Robust identity and access management form the foundation of ERP security. This includes implementing multi-factor authentication for all ERP access, role-based access controls that align with business functions and segregation of duties requirements, regular access reviews and certification processes, and automated provisioning and deprovisioning tied to HR systems.
Advanced ERP security implementations should include privileged access management for administrative functions, just-in-time access for sensitive operations, and comprehensive monitoring of all user activities within the ERP environment.
Data Protection and Encryption
ERP systems require comprehensive data protection strategies that address both structured and unstructured data. This includes implementing encryption for sensitive data at rest within ERP databases, securing data in transit between ERP components and external systems, and managing encryption keys separately from encrypted data.
Consider implementing database activity monitoring, data loss prevention tools integrated with ERP workflows, and field-level encryption for highly sensitive data elements like social security numbers, payment information, and proprietary business data.
Network Security and Architecture
ERP systems should be deployed within secure network architectures that include network segmentation to isolate ERP environments from other business systems, firewalls, and intrusion detection systems specifically configured for ERP traffic patterns, and regular vulnerability assessments focused on ERP infrastructure components.
Cloud-based ERP deployments require additional attention to secure configuration of cloud resources, proper implementation of virtual private networks, and ongoing monitoring of cloud security posture.
Application Security
ERP applications themselves require specific security measures, including regular security patch management coordinated with business operations, secure configuration of ERP modules and interfaces, and implementation of application-level security controls like input validation and output encoding.
Custom ERP modifications and integrations should undergo security code reviews, and third-party add-ons should be evaluated for security risks before implementation.
ERP Vendor Management and Risk Assessment
Cloud ERP Security Considerations
Organizations adopting cloud-based ERP solutions must carefully evaluate vendor security capabilities and shared responsibility models. This includes reviewing vendor security certifications like SOC 2 Type II reports, understanding data residency and sovereignty implications, and ensuring proper configuration of cloud security controls.
Key considerations include backup and disaster recovery capabilities, incident response procedures, and the vendor’s ability to support compliance requirements specific to your industry.
On-Premises ERP Security Management
Organizations maintaining on-premises ERP deployments face different challenges, including managing infrastructure security, maintaining current security patches and updates, and implementing proper physical security controls for ERP servers and databases.
This also includes managing relationships with implementation partners, system integrators, and support vendors who may require access to ERP environments.
Vendor Risk Assessment
Comprehensive vendor risk assessments should evaluate financial stability, security practices, compliance certifications, and incident response capabilities. Regular reassessment ensures ongoing vendor performance meets security and compliance expectations.
Data Governance in ERP Environments
Data Classification and Management
Effective ERP data governance begins with comprehensive data classification that identifies different types of sensitive information processed by various ERP modules. This includes financial data, personal information, intellectual property, and regulatory data that may require special handling procedures.
Implement data retention policies that align with regulatory requirements and business needs, ensuring proper disposal of data when retention periods expire and maintaining audit trails of data lifecycle management activities.
Business Process Controls
ERP systems enable complex business processes that must be designed with appropriate controls and oversight. This includes implementing approval workflows that enforce segregation of duties, maintaining audit trails for all business transactions, and regularly reviewing process controls for effectiveness.
Consider implementing continuous monitoring tools that can identify unusual patterns or potential fraud indicators within ERP business processes.
Integration Security
ERP systems typically integrate with numerous other business applications, creating complex data flows that must be secured and monitored. This includes securing APIs and web services used for ERP integrations, implementing proper authentication and authorization for system-to-system communications, and monitoring data exchanges for anomalies.
Implementation and Management Best Practices
Security-First ERP Implementation
When implementing new ERP systems or upgrading existing ones, security should be a primary consideration throughout the project lifecycle. This includes conducting threat modeling exercises during the design phase, implementing security controls during system configuration, and performing comprehensive security testing before go-live.
Develop security requirements that align with your compliance obligations and risk tolerance, and ensure these requirements are incorporated into vendor contracts and implementation agreements.
Change Management and Configuration Control
ERP systems require ongoing modifications to support changing business needs, but these changes must be managed carefully to maintain security and compliance. Implement formal change management processes that include security impact assessments, testing procedures for all changes, and rollback plans in case of issues.
Maintain configuration baselines and implement automated monitoring to detect unauthorized changes to critical ERP settings.
User Training and Awareness
ERP users require specific training on security procedures, compliance requirements, and proper data handling practices. This includes initial training during user onboarding, regular refresher training to address new threats and requirements, and specialized training for users with privileged access or sensitive responsibilities.
Consider implementing security awareness campaigns that highlight ERP-specific risks and best practices.
Incident Response for ERP Environments
ERP-Specific Incident Response
Develop incident response procedures specifically tailored to ERP environments, considering the critical nature of ERP systems to business operations and the potential for widespread impact from ERP security incidents.
This includes establishing clear escalation procedures, defining roles and responsibilities for incident response team members, and maintaining communication plans that address both internal stakeholders and external parties, including regulators and customers.
Business Continuity Planning
ERP systems are often critical to business operations, making business continuity planning essential for managing security incidents. This includes maintaining current backup and recovery procedures, testing disaster recovery plans regularly, and developing procedures for operating business processes during ERP system outages.
Consider implementing redundant systems or alternative processes that can maintain critical business functions during extended ERP outages.
Future Trends in ERP Security and Compliance
Artificial Intelligence and Machine Learning
AI and ML capabilities are increasingly integrated into ERP systems, creating new opportunities for improved security monitoring and threat detection while also introducing new risks and compliance considerations.
Organizations should consider the implications of AI-driven decision-making within ERP processes, ensuring transparency and explainability requirements are met and that AI systems don’t introduce bias or discrimination into business processes.
Zero Trust Architecture
Zero-trust security models are particularly relevant for ERP environments, which often integrate with numerous systems and support remote access by various user types. Implementing zero trust principles can improve ERP security by eliminating implicit trust and continuously verifying all access requests.
Regulatory Evolution
The regulatory landscape continues to evolve, with new privacy laws, cybersecurity requirements, and industry-specific regulations emerging regularly. Organizations should stay informed about regulatory developments that may impact their ERP systems and compliance obligations.
Conclusion
Compliance and data security in ERP systems represent a critical success factor for businesses. The centralized nature of ERP systems, combined with their integration across business functions, creates both tremendous operational benefits and significant risk exposure that must be carefully managed.
The investment in proper ERP security and compliance management and contact ERP experts to operational efficiency, stakeholder trust, and competitive advantage.
The organizations that succeed will be those that view security and compliance not as constraints but as enablers of sustainable business growth and innovation.
Table of contents
- Why ERP Security and Compliance Matter More Than Ever
- Critical US Compliance Frameworks for ERP Systems
- Essential Security Controls for ERP Systems
- ERP Vendor Management and Risk Assessment
- Data Governance in ERP Environments
- Implementation and Management Best Practices
- Incident Response for ERP Environments
- Future Trends in ERP Security and Compliance
- Conclusion

Related Articles







